Shop
-0%
18,99 € Ursprünglicher Preis war: 18,99 €
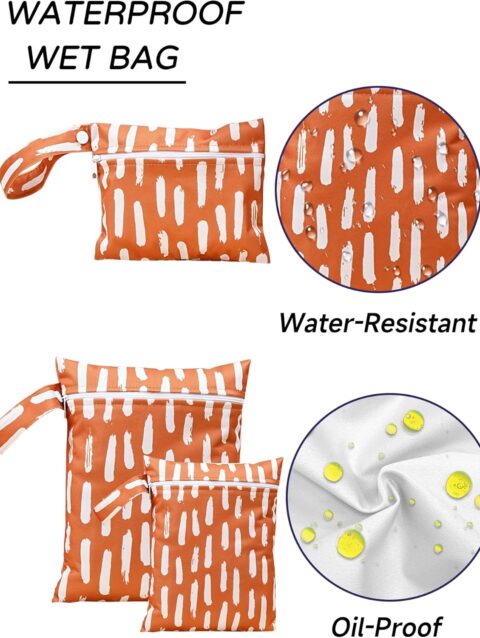
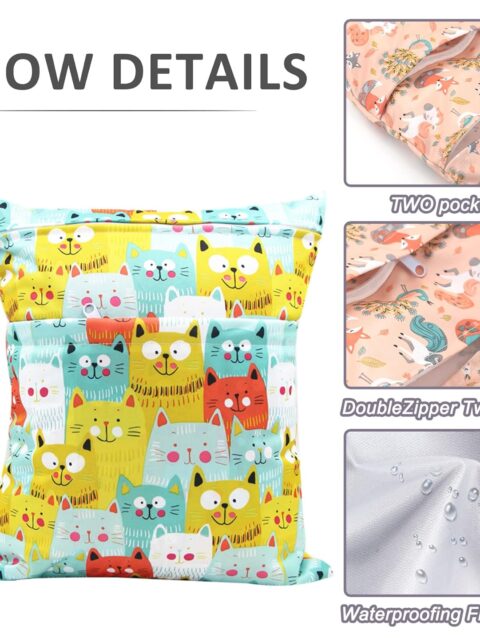
Maeau Wetbags für Stoffwindeln Windeltasche Wickeltasche Baby Wetbag Organiser Beutel Nasstaschen Kindergarten Nassbeutel Wiederverwendbare Wetbag Waschbar Gym Bag
18,04 €Aktueller Preis ist: 18,04 €.8